IFIP WG 11.9 ICDF 2024 - Paper accepted and presented
8 Januar 2024
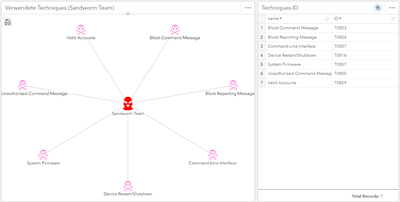
Our article on Usable and Assessable Generation of Forensic Data Sets Containing Anti-Forensic Traces at the Filesystem Level was accepted and presented at the IFIP WG 11.9 International Conference on Digital Forensics (ICDF) 2024. The article presents a novel approach to automatically generate forensically relevant (anti-forensic) traces on the file system level and combine these file system dumps with other relevant traces generated in the operating system. The paper was presented at the IFIP WG 11.9 ICDF 2024 on January 5th 2024 in New Delhi (India).
Authors: Thomas Göbel, Harald Baier and Jan Türr (Universität der Bundeswehr München)
Abstract:
Digital forensics and anti-forensics are important parts of cybersecurity as they provide vital information used to create preventive and reactive measures. To enable digital forensic tool validation as well as meaningful educational study materials and research in these fields, diverse and realistic data sets are needed, which reflect anti-forensic measures, too. However, due to different reasons like privacy issues or legal obstacles data sets are more and more synthesised. This work contributes threefold to the improvement of the digital forensic process by assessing anti-forensic measures on the file system level and providing a usable proof of concept to synthesise appropriate data sets containing anti-forensic activities. First, we provide an in-depth analysis of anti-forensic data hiding techniques within the evolving Linux-based btrfs file system. Second, we provide a proof of concept to generate anti-forensic traces on the file system level within a post-mortem storage device data set. Our proof of concept links two existing frameworks, namely the data synthesis framework ForTrace and the anti-forensic data hiding framework fishy. As a result, we provide a usable data synthesis tool that is able to generate anti-forensic data hiding traces for the three common file systems NTFS, ext4, and btrfs, and in combination also provides essential other data synthesis functionality to simulate the normal behaviour of the operating system. As a third contribution, we introduce three attacker models to assess the respective anti-forensic data hiding techniques. Overall, we provide a usable possibility to generate data sets that reflect anti-forensic artefacts as potentially used by attackers.